By Kailin Acheson
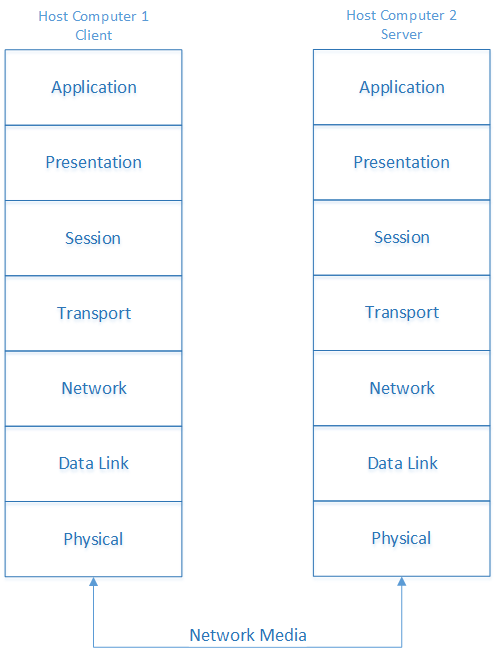
In Part I of The Seven Layers of Networking blog, John began a discussion about the layers of the Open Systems Interconnection (OSI) model. The first four layers, which you can read about in that blog, are the Physical layer, the Data Link layer, the Network layer, and the Transport layer. In network discussions, you'll most often encounter the first four layers. The final three layers, the Session layer, the Presentation layer, and the Application layer, are not as commonly discussed but are still essential to a network. This blog will cover those three layers and the encapsulation process that occurs when one host communicates with another. Then you'll have to stay tuned for Part III, which will cover a related-yet-different layered model, the Transmission Control Protocol/Internet Protocol (TCP/IP) model.
The Seven Layers of Networking – Part II
Mar 25, 2014 2:29:00 PM / by Kelson Lawrence posted in application layer, encapsulation within layers, presentation layer, Seven Layers of Networking Part 2, session layer
.NET Quest, Part IV: Installing Boson Software in Oracle VirtualBox
Mar 19, 2014 9:04:00 AM / by Kelson Lawrence posted in .NET Quest
By James Hanback
Very few Sierra On-line adventure games from the 1980s and early 1990s contained the kind of first-person shooter action that would later come to dominate the PC gaming landscape. Mostly, the Sierra adventure gamer had to rely on his or her wits, knowledge, and perhaps the printed manual to piece together the clues that would eventually lead to the game’s solution. Some games, like Police Quest, required some real-life knowledge of police procedure to even get past the parking lot of the fictional Lytton, Calif., police station. Others, like Conquests of Camelot, required some research into arcane flower symbolism (which was helpfully documented in the game’s printed manual, the Liber Ex Doctrina). Similarly, you might find that you need to rely a little more on your own knowledge of your computer hardware to complete this phase of our adventure as we restore our game from the previous three posts and continue our quest to use Boson software in a non-Windows environment.
MS Windows 7 Tips and Tricks | 2.8.4 EFS – Part 2
Mar 5, 2014 8:25:00 AM / by Kelson Lawrence posted in file encryption key, Encrypting File System
2.8.4 EFS – Part 2
By Val Bakh
In part 1 of the blog post about Encrypting File System (EFS), we described how EFS works, in common-sense terms, using a story of your attempts to secure the door of your house as a convenient example. Now let’s continue this discussion and translate that story into technical terms. We’ll also talk about certificates because they are virtually inseparable from matters related to encryption.