By Delana Hallstedt
What makes a solid-state drive faster?
Immobility.
Yep, it’s really as simple as that.
I don’t mean that in a portability sort of way; solid-state drives (SSDs) are quite portable! An SSD doesn’t move on the inside, and this lack of movement is what helps it perform so much faster than other storage devices. Having said that, it really wouldn’t be much of a blog post if I didn’t attempt to paint you some sort of similitude packed with a sampling of picturesque details that will assist you in a greater depth of understanding of just how this all works…right?
Kelson Lawrence
Recent Posts
What makes a solid-state drive faster?
Jul 8, 2013 2:30:00 PM / by Kelson Lawrence posted in Delana Hallstedt, solid-state drive, fast, immobility, SSD, SSDs
What Is Two-Factor Authentication and Why Do I Need It?
Jun 18, 2013 9:06:00 AM / by Kelson Lawrence posted in Two-Factor Authentication, password recovery techniques, social engineering
By James Hanback
Just when you thought it was safe to pull the curtains back from the windows and let the sun shine in on the bodies of all the defeated zombies of the weak password apocalypse, you find out that they're not really dead. You shored up your devices, your Internet accounts, and maybe even the combination on your locker at the gym with the strongest, most secure mixture of characters you could conceive. Nobody can guess them. Nobody can brute force crack them. You're gold, right?
What are the differences between an IPSec VPN and a GRE tunnel?
Jun 5, 2013 8:53:00 AM / by Kelson Lawrence posted in VPN vs GRE, differences between VPN and GRE
By Tim Charlton
IP Security (IPSec) Virtual Private Networks (VPNs) and Generic Routing Encapsulation (GRE) tunnels are both methods for transferring data across public, intermediary networks, such as the Internet. However, there are considerable differences between the two technologies. Let’s start with a brief overview.
MS Windows Tips and Tricks | 2.7.4 IE Security Features
May 16, 2013 12:54:00 PM / by Kelson Lawrence posted in Internet Explorer Security Features, InPrivate Browsing, Safety menu
By Val Bakh
2.7.4 Internet Explorer Security Features
The Internet has become an integral part of our lives. Nowadays, the Internet gives us access to e-mail, instant messaging, telephone, television, banking, shopping, research—you name it. It is so completely woven into nearly everything we do so that most of the time we don’t even think of it as something external, something that we need to connect to before we can make use of it. That is, of course, until something goes wrong. The Internet is not only a convenience; it is also a potential danger.
What’s an ARP?
May 9, 2013 8:21:00 AM / by Kelson Lawrence posted in Delana Hallstedt, ARP, What is ARP?, Address Resolution Protocol
By Delana Hallstedt
My initial plan for this blog post was to attempt to unravel the alphabet soup approach to all things technology related – Why so many acronyms?!? However, upon doing a little bit of research on the origins of acronyms (retronyms, neologism, and alphabetism oh my!), I quickly talked myself out of that and settled on one particular acronym.
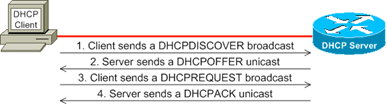
A Cisco Administrator’s Guide to DHCP
May 1, 2013 1:28:00 PM / by Kelson Lawrence posted in DHCP Relay Agent, Guide to DHCP, DHCP, DHCP pool, DHCP leases
By Amy Haigh
As a network administrator, you will be responsible for ensuring that each host on your network is configured with the appropriate TCP/IP parameters to communicate with other hosts. To communicate on a network, either private or public, a host must be configured with — at minimum — an IP address, a subnet mask, and a default gateway. On a small private network with consistent hosts, you can manually configure these options on each host. But if you administer a large network, or even a small network where laptops and tablets continuously connect and disconnect, you will find implementing Dynamic Host Configuration Protocol (DHCP) to be a lifesaver.
MS Windows Tips and Tricks | 2.7.3 Windows XP Mode
Apr 25, 2013 11:14:00 AM / by Kelson Lawrence posted in Windows XP Mode, XPM, Windows Virtual PC (VPC)
2.7.3 Windows XP Mode
By Val Bakh
We don’t talk much of Windows Vista nowadays. It didn’t stay on the market very long and was soon replaced with a “new-and-improved” version, Windows 7. The important fact, however, is that Windows Vista was the first of the new generation of Microsoft’s operating systems. The move from Windows XP to Windows Vista and Windows 7 is perhaps even more significant than the long-forgotten departure from Windows NT in favor of Windows 2000. In the big scheme of things, Windows 2000 brought us Active Directory, but from a regular user’s perspective, the change was not all that significant: a prettier graphical user interface (GUI), but not much difference in the applications that users could run. Windows XP added a few new bells and whistles but did not hinder our ability to run most of our favorite legacy applications.
Network Security Part 2: Threats
Apr 23, 2013 8:10:00 AM / by Kelson Lawrence posted in physical threats, reconnaissance attacks, access attacks, hardware threats, environmental threats, administrative threats, Network Security, electrical threats
By Kailin Acheson
If you are a network administrator, you might be familiar with various types of attacks that malicious users might launch against the network in an attempt to destroy it. These attacks, described in Network Security Part 1: Attacks, include passive, active, close-in, insider, and distribution attacks. As a network administrator, you should also be familiar with possible threats to the network. These include physical threats, reconnaissance attacks, and access attacks.
Network Security Part 1: Attacks
Apr 17, 2013 8:44:00 AM / by Kelson Lawrence posted in active attacks, close-in attacks, distribution attacks, Network Security, passive attacks, insider attacks
By Kailin Acheson
If you are the administrator of a network, you likely have been thinking about, and possibly worrying about, potential network attacks. It's much more rewarding (and less stressful) to protect a network than to fix it (unless, as Tim Charlton wrote in one of his recent blogs, you like the pressure. It might be helpful to try to answer the following questions as you consider attacks on the network:
The New 200-101 ICND2 Exam: Changes and Thoughts
Apr 9, 2013 8:42:00 AM / by Kelson Lawrence posted in CCNA, ICND2 Revision
By James Hanback
You've spent all these weeks and some of your hard-earned cash studying for Cisco's 640-816 ICND2 exam only to discover that there's a brand new Cisco Certified Network Associate (CCNA) version 2.0 track. Cisco's 200-101 exam, along with its 100-101 ICND1 prerequisite, was announced on March 26 and is now available to candidates pursuing CCNA certification or recertification. Cisco also released a new version 2.0 of the composite exam, which is numbered 200-120. Among the many questions these new developments raise in your mind as you consider heaving your old 640-816 study guide toward the trash bin might be "Have I wasted my time studying for 640-816?"