2.8.4 EFS – Part 2
By Val Bakh
In part 1 of the blog post about Encrypting File System (EFS), we described how EFS works, in common-sense terms, using a story of your attempts to secure the door of your house as a convenient example. Now let’s continue this discussion and translate that story into technical terms. We’ll also talk about certificates because they are virtually inseparable from matters related to encryption.
Kelson Lawrence
Recent Posts
MS Windows 7 Tips and Tricks | 2.8.4 EFS – Part 2
Mar 5, 2014 8:25:00 AM / by Kelson Lawrence posted in file encryption key, Encrypting File System
.NET Quest, Part III: Installing Boson Software in Parallels Desktop for Mac
Feb 18, 2014 4:19:00 PM / by Kelson Lawrence posted in .NET Quest, Mac
By James Hanback
As 1980s home computing graphics technology improved and paved the way for the early 1990s, so did the animated graphical adventure worlds created by Sierra On-Line grow more detailed and artistically rendered. By the time the first King’s Quest was unleashed upon the world, Color Graphics Adapter (CGA) technology had given way to Enhanced Graphics Adapter (EGA) technology. By the early 1990s, EGA gave way to Video Graphics Array (VGA) technology. More pixels and more colors meant a better level of detail for the gamer. VGA graphics were such an improvement over previous display technologies that Sierra actually rereleased some of its classic games with updated graphics and some modified play. Instead of typing commands to interact with the game, you could use a mouse to select icons or tools that you could apply to the character to make him or her perform actions in the game. However, some gamers—your humble co-adventurer among them—actually preferred the older command interpreter-style play of those first editions.
.NET Quest, Part II: Installing Boson Software in VMware Fusion
Feb 12, 2014 8:50:00 AM / by Kelson Lawrence posted in .NET Quest, Installing Boson in VMware Fusion
By James Hanback
It probably came as no surprise to the developers of mid-1980s computer role-playing adventure games like King’s Quest that some players might get impatient, frustrated, or just plain stuck while trying to decipher the varied solutions to the puzzles they encountered along the way. In fact, guides to completing such games, known as walk-throughs, became a clever way to make a little bit of additional revenue on the sale of a game. For many games, you could purchase a printed walk-through. Some of them even came with little red cellophane decoders that enabled you to reveal only specific clues to yourself as you followed along, thus allowing you to preserve some of the mystery of playing the game without a guide. Late in the decade, there were also some automated 1-900 hint lines you could call that, for a per-minute fee, would guide you through the particular part of the game that was frustrating you. These days, of course, you can get all the walk-through you need for free on the Internet. Back in 1984, the term Internet had only been around for a couple of years and the world’s first Web browser was still six years away.
.NET Quest, Part I: Installing Boson Software in a non-Windows Environment
Jan 21, 2014 9:34:00 AM / by Kelson Lawrence posted in Dual Boot, Wine, Virtualization
By James Hanback
If you were ever into mid-1980s computer gaming, you might know about a little graphical computer adventure game called King’s Quest. At the time, the game was developed and distributed by a company known as Sierra On-Line. King’s Quest was a role-playing adventure game, which meant that your goal as player was to guide the main character, Sir Graham, through the three-dimensional computer-generated Kingdom of Daventry. You walked Sir Graham around Daventry (and beyond) by using the keyboard. You made him perform other actions by typing verb and noun combinations or phrases like “take mirror” to gather items you would later use to solve puzzles that eventually (hopefully) enabled you to solve the game’s ultimate objective. Sometimes the game’s interpreter couldn’t figure out what you were telling Sir Graham to do, and those were the times that you’d need to get creative.
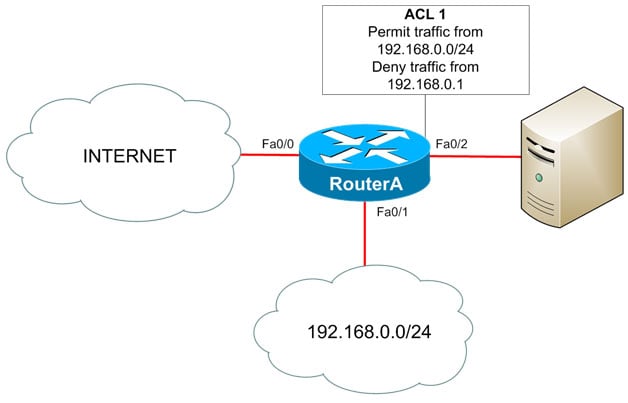
ACL Basics
Jan 14, 2014 3:45:00 PM / by Kelson Lawrence posted in Delana Hallstedt, permit, deny, syntax access-list, ACL basics, dysfunctinoal access control lists, standard ACLs, implicit deny rule
By Delana Hallstedt
If I were to start a conversation with my husband about a “broken ACL,” he would immediately panic and begin searching the Web for evidence that his beloved Megatron was free from injury and that his anterior cruciate ligament (ACL) was in perfect working order. Especially this time of year! Although I’m rather fond of the guy myself, for fantasy football purposes, that’s not the sort of ACL I’d most likely be referring to.
MS Windows 7 Tips and Tricks | 2.8.3 EFS – Part 1
Jan 9, 2014 8:39:00 AM / by Kelson Lawrence posted in NTFS, Encrypting File System, EFS Part 1
2.8.3 EFS – Part 1
By Val Bakh
As the world of information technology (IT) becomes more and more sophisticated with each passing day, the security of the information that we store on computers has become a major headache. But, just as we occasionally have to go to work while suffering a migraine, we have to accept the pervasive need for IT security. There’s no way around it. It’s like locking the door to your house when you are leaving for work. There’s always the risk that you might misplace your house keys during the day or leave them behind in your office, but leaving the door unlocked is no longer as viable an option as it used to be a few decades ago. Similarly, we have to secure our data. The question is, how? Data security is an extremely complex but fascinating subject area. There are many technologies and methods, which are usually implemented in conjunction with one another to form a multilayered, impregnable (keep your fingers crossed) fortress.
13 in '13 | Recapping the Year at Boson
Jan 2, 2014 9:10:00 AM / by Kelson Lawrence posted in certification, practice exams, courseware
By Kailin Acheson
2013 has flown by, and 2014 (our 15th anniversary!) is close on its heels. As we start the new year, I thought I'd share my top 13 highlights from the Boson World in 2013.
Much Ado About Noting OSPF Area IDs in Dotted Decimal Format
Nov 21, 2013 8:20:00 AM / by Kelson Lawrence posted in Noting OSPF Area IDs in Dotted Decimal Format
By James Hanback
Time for a pop quiz. You have less than one second. Shout out the first term that pops in your head when you examine the following string of characters:
How to Activate and Use Boson’s Digital CCNA Courseware
Oct 23, 2013 9:51:00 AM / by Kelson Lawrence posted in activating digital CCNA Courseware, javelin reader, activating ccna curriculum
By James Hanback
Back in the early aughts I could sometimes be seen lugging around gargantuan certification study guides that—once I obtained certification—ended up either creating a sizable footprint on my reference shelf or propping my bedroom door open at night. Although printed books have been and always will be a convenient means of carrying information with you, tomes such as certification study guides can be cumbersome to juggle alongside your briefcase, your laptop bag, your lunch, and the various mobile devices you carry along on your daily jaunt through this thing called modern life. Nevermind trying to maintain that balancing act while crossing a busy intersection, trying to jam your car keys into your pocket or purse, and keeping yourself dry of the hot coffee that’s sloshing around in your travel mug.
MS Windows Tips and Tricks | 2.8.2. Windows Firewall – Part 2
Oct 2, 2013 12:25:00 PM / by Kelson Lawrence posted in Windows Firewall, WF, scope, block edge traversal, part 2, protocols and ports, programs and services, edge traversal
2.8.2. Windows Firewall – Part 2
By Val Bakh
In last month’s blog post about Windows Firewall (WF), we introduced network firewalls and host-based firewalls and explained the general principles of their operation. We also became acquainted with WF, its most important general settings, and two types of rules. Now we’ll discuss both types of WF rules and examine their main settings. We will also consider an example scenario that illustrates how the two types of rules work together.